#hardware encryption key
Explore tagged Tumblr posts
Text

Oh yes — that’s the legendary CIA Triad in cybersecurity. It’s not about spies, but about the three core principles of keeping information secure. Let’s break it down with some flair:

⸻
1. Confidentiality
Goal: Keep data private — away from unauthorized eyes.
Think of it like locking away secrets in a vault. Only the right people should have the keys.
Examples:
• Encryption
• Access controls
• Two-factor authentication (2FA)
• Data classification
Threats to it:
• Data breaches
• Shoulder surfing
• Insider threats
⸻
2. Integrity
Goal: Ensure data is accurate and trustworthy.
No tampering, no unauthorized changes — the data you see is exactly how it was meant to be.
Examples:
• Checksums & hashes
• Digital signatures
• Version control
• Audit logs
Threats to it:
• Malware modifying files
• Man-in-the-middle attacks
• Corrupted files from system failures
⸻
3. Availability
Goal: Data and systems are accessible when needed.
No point in having perfect data if you can’t get to it, right?
Examples:
• Redundant systems
• Backup power & data
• Load balancing
• DDoS mitigation tools
Threats to it:
• Denial-of-service (DoS/DDoS) attacks
• Natural disasters
• Hardware failure
⸻
Why it matters?
Every cybersecurity policy, tool, and defense strategy is (or should be) built to support the CIA Triad. If any one of these pillars breaks, your system’s security is toast.
Want to see how the CIA Triad applies to real-world hacking cases or a breakdown of how you’d protect a small business network using the Triad? I got you — just say the word.
29 notes
·
View notes
Text
Cyber / Virtual ID Pack

Inside this pack, you will find: Pronouns, Titles, Names, and Genders that relate to Virtuality, Cybernetic, Robots, and anything alike!
This features a LOOOONG list of pronouns and dystopian-ish names!

Pronouns:
Cy/Cyb/Cyber/Cybers/Cyberself
Vir/Virt/Virtual/Virtuals/Virtualself
Ne/Net/Network/Networks/Networkself
Ne/Net/Nets/Nets/Netself
In/Inter/Internet/Internets/Internetself
Co/Comp/Computer/Computers/Computerself
In/Inpu/Input/Inputs/Inputself
Ou/Out/Output/Outputs/Outputself
Vi/Viru/Virus/Viruses/Virusself
Anti/Antivir/Antivirus/Antiviruses/Antivirusself
Er/Erro/Error/Errors/Errorself
Sys/Syste/System/Systems/Systemself
Pro/Proce/Processor/Processors/Processorself
Di/Digi/Digital/Digitals/Digitalself
Do/Down/Download/Downloads/Downloadself
Up/Uplo/Upload/Uploads/Uploadself
Cor/Corru/Corrupt/Corrupts/Corruptself
Mal/Malwa/Malware/Malwares/Malwareself
Se/Secur/Security/Securitys/Securityself
Cry/Crypt/Crypto/Cryptos/Cryptoself
We/Web/Webs/Webs/Webself
Web/Webs/Website/Websites/Websiteself
Fu/Futu/Future/Futures/Futureself
Ro/Rob/Robot/Robots/Robotself
Rob/Robo/Robotic/Robotics/Roboticself
By/Byt/Byte/Bytes/Byteself
Fi/Fil/File/Files/Fileself
Ra/Ram/Rams/Rams/Ramself
Scr/Scre/Screen/Screens/Screenself
Te/Tech/Techs/Techs/Techself
Te/Tech/Techno/Technos/Technoself
Tec/Techno/Technology/Technologys/Technologyself
Ma/Mach/Machine/Machines/Machineself
Wi/Wir/Wire/Wires/Wireself
Na/Nan/Nano/Nanos/Nanoself
Da/Dat/Data/Datas/Dataself
Plu/Plug/Plugs/Plugs/Plugself
Ele/Elect/Electric/Electrics/Electricself
Ke/Key/Keys/Keys/Keyself
Pa/Pass/Password/Passwords/Passwordself
Ter/Term/Terminal/Terminals/Terminalself
Cy/Cybo/Cyborg/Cyborgs/Cyborgself
Ty/Typ/Type/Types/Typeself
Fi/Firm/Firmware/Firmwares/Firmwareself
Ha/Hard/Hardware/Hardwares/Hardwareself
So/Soft/Software/Softwares/Softwareself
Ha/Hack/Hacks/Hacks/Hackself
Ha/Hack/Hacker/Hackers/Hackerself
Si/Sig/Signal/Signals/Signalself
Clo/Clou/Cloud/Clouds/Cloudself
On/Onli/Online/Onlines/Onlineself
In/Insta/Install/Installs/Installself
Co/Cod/Code/Codes/Codeself
Ad/Admi/Admin/Admins/Adminself
Gra/Graph/Graphic/Graphs/Graphself
Sy/Syn/Synth/Synths/Synthself
Phi/Phis/Phish/Phishs/Phishself
Phi/Phish/Phishing/Phishings/Phishingself
Do/Dox/Doxs/Doxs/Doxself
Si/Sit/Site/Sites/Siteself
Bo/Bot/Bots/Bots/Botself
Pho/Phon/Phone/Phones/Phoneself
Key/Keyboa/Keyboard/Keyboards/Keyboardself
Mo/Mou/Mouse/Mouses/Mouseself
Chi/Chip/Chips/Chips/Chipself
Moth/Mother/Motherboard/Motherboards/Motherboardself
Co/Com/Compute/Computes/Computeself
Pi/Pira/Piracy/Piracys/Piracyself
En/Encry/Encrypt/Encrypts/Encryptself
PDA/PDAs
CPU/CPUs
URL/URLs
404/404s
📱/📱's
💻/💻's
⌨️/⌨️'s
🖥/🖥's
🖱/🖱's
💿/💿's
🎙/🎙's

Titles:
The Cyborg
(X) Whos Wired
Made of Nanotech
(X) Who Uses Nanotech
Scholar of Machines
The Cyber Security
(X) Who Has Cyber Wings
Connected Online
Offline
Unable to Connect
The Administrator
Synthesizer
The Hacker
Nanohacker
The Antivirus
Reconnecting...
ERROR: Unable to Connect
ERROR 404
ERROR: Malware Detected

Names:
Since names don't usually have "techy" meanings, I picked one's that sounded the most cybernetic, cyberpunkish, dystopian, virtualish, etc!
Fem: Althea, Ameris, Astoria, Arcadia, Astra, Beretta, Cyra, Crystal, Crosselle, Eve, Io, Jinx, Kit, Lilith, Meridian, Morrian, Nebula, Nova, Neve, Noxia, North, Octavia, Odette, Odile, Prota, Pistol, Rey, Rue, Rain, Raine, Stormy, Seraphina, Sona, Skye, Thundra, Tempest, Vega, Viva, Vinette, Venus, Xenia, Xya, Xena, Xiomara, Xenara, Xanthe, Zephyria, Zyla, Zadie, Zia,
Masc: Alaric, Aksel, Arden, Antares, Apollo, Ace, Asher, Cole, Cyrus, Code, Draven, Drift, Ender, Flynn, Hawk, Isaac, Jericho, Kip, Kai, Koios, Knox, Nox, Neo, Nero, Octavian, Orionis, Oghma, Paine, Rocket, Ray, Rai, Silas, Slader, Sebastian, Seth, Seraphim, Thalax, Theo, Thatch, Vox, Vector, Wyatt, Xyon, Xane, Xylan, Xerxes, Xayden, Xavier, Xander, Zander, Zayden, Zenith, Zev, Zale, Zane, Zaire, Zeke,
Neu: Andras, Axe, Axiom, Alloy, Allele, Ash, Arrow, Beetle, Chrom, Corvus, Dakota, Dell, Eos, Echo, Eden, Fox, Ghost, Glöckner, Hydrae, Ion, Jesper, Jett, Kursk, Lesath, Locklyn, Lyrae, Maddox, Nemo, Orca, Onyx, Oxygen, Panther, Rikko, Robin, Rune, Scorpion, Scorpius, Saturn, Sparrow, Sonar, Tore, Tauri, Techne, Techno, Ursae, Vesper, Volt, West, Wolf, Xen, Xenon, Zephyr, Zodiac, Zenon, Zeru, Zero, Zen

Genders:
Futuracityc: A gender related to futuristic cities
Futurafashic: A gender related to futuristic fashion
Futurahousic: A gender related to futuristic houses
Digigender: A digital gender. Rangeable from any digital thing or file; virus, malware, .txt, .mp3, antivirus, trojan, email, etc.
Cybergender: A gender or form of gender expression where ones gender or expression is deeply tied into Cyberpunk lore, culture, fashion or media.
CYBERWEAPONIC - a gender that feels like a digital or robotic weapon. this gender may also have ties to sentient AI used as a weapon, but not necessarily.
BIOAMOROBOTIC - a gender connected to being a robot who loves humanity and the world and finds joy all around them!
RobAnatomic - a gender under the anatomic system(link) related to robots, anatomy, robotic anatomy, the anatomy of robots, robots made to teach/study anatomy, anatomy based/related robots of some kind, the anatomy/biology of someone or something being robotic, having robotic anatomy, being a robot with an interest in anatomy and more.
Robogender - for people who’s gender identity aligns with machines/robots/androids/mechs/AIs.
Cyborwebic - a gender related to webcore, evil scientist aesthetics, artificial beings such as androids/cyborgs etc, turtleneck sweaters and old computer monitors
AI flag - this can be used for nonhuman, otherkin, gender, delusion.
Gendervirtual / Genderdigital - a gendersystem in which your gender is related to virtual ) digital themes and x , such as being a virtual ) digital x , a x who loves virtual ) digital themes , a virtual ) digital being who loves x themes , etc.
#npt ideas#npt blog#npt pack#npt list#npt suggestions#cyber npt#virtual npt#robotic npt#robot npt#cybergender#virtualgender#robotgender#digitalgender
55 notes
·
View notes
Text
Left for Dead
Part One
Scott Tracy breathed a sigh of relief as he felt the wheels of the ‘conventional’ jet he was flying left the tarmac.
His never failed to feel lighter once he was no longer touching the earth, but this time the relief was more intense than usual.
As he guided the executive jet – once Jeff’s favourite plane, a sleek long-haul commercial jet that had been the Aviation arm of Tracy Industries flagship product, and dubbed ‘Tracy One’ – exactly through the ‘gateway’ at the end of the runway climb out, the radio crackled to live. The heavily accented English of the Departures Controller for Trondheim Lufthavn gave him his final instructions to clear the Lufthavn’s controlled airspace and join his filed flightpath out of Norway and back to Tracy Island.
He only let himself relax as he hit his cruising speed and altitude, and activated the pre-programmed autopilot.
Reaching back he caught the retractable tray table and dragged it towards him, before picking up his insulated mug, a custom-made gift from Brains that allowed him to ensure he had hot coffee available on a solo flight in the plane.
He couldn’t help glancing back at the safe built into the bulkhead at the back of the cockpit. He still had grave reservations about getting TI involved in the construction of the World Government’s new high-security computer system to be based in Norway; but the World Government had wanted Tracy Industries for their reputation for excellence and security, the TI Board wanted it, and most importantly John wanted it.
Scott tried not to think about the fact that his brother was likely to include a backdoor to the system.
But Scott had been convinced that it was in the best interests of all involved to take the project on, and he had gone to Norway to meet the key personnel and personally take receipt of the plans. TI facilities would produce the various key components and they would be shipped to Tracy Island for construction by one Hiram K. Hackenbacker
Scott sighed, even Brains had been excited by the prospect of getting to look at the designs, and the attendant programming that the hardware would be running. Something about the specifications for the “new ‘unbreakable’ encryption protocols”, and “the next major breakthrough in computing, practically quantum!”
Scott was worried that the two – three if Alan inserted himself into the mix – computer nerds would back-engineer the TOP SECRET computer and incorporate it into International Rescue’s equipment.
When – and Scott was not an optimist when it came to this sort of things, so it was when and not if – the rest of the world figured out that they had that technology, there would be some uncomfortable questions that Scott would be left to try to answer.
And he was resolutely NOT thinking about what Eos could do with all that processing power. Scott had reached a truce with the Space Monitor’s pet AI, but he hadn’t made peace with it … her. She had come dangerously close to killing John, ‘misunderstanding’ or not, ‘self-defence’ or not.
Harming his family was the one sin Scott Tracy could not forgive.
The next hour or so disappeared quietly as Scott brooded on his misgivings, carefully watched the plane’s gauges, and the sky.
Sometime after the onboard computer indicated that it had successfully completed its mandatory handshake with Chinese Air Control Scott stretched, arching his back and spreading his toes within the confines of his shoes. Flying alone was great for relaxation, flying alone long distances however … no matter how good the autopilot, a good pilot never left the controls unmanned.
Tracy One, while fast, was no Thunderbird One. I’m getting soft, Scott thought bemused. Too used to the multiple mach speed of his usual means of transportation.
Settling back into his seat, Scott once more scanned the gauges … only to see them all fade out as the engines whined their rollback to idle and shutdown.
Scott swore, unbelieving, hands once more on the controls, as he quickly hit two buttons, setting his transponder to squawk distress mode, and deploying the RAT, a small drop down wind turbine that dropped from the planes undercarriage and caught the airflow, generating enough power to get some gauges and controls working.
Fingers automatically worked at the controls, reconfigure for maximum glide, run through the midair engine restart procedure. And …
Nothing.
As Scott immediately recommenced the restart, he was on the radio: “Mayday, Mayday, Maday. This is November Tango India Zero One Charlie. Twin engine roll back, loss of power. Attempting restarts. Requesting assistance to squawk location.”
No response. Scott cycled through another engine restart attempt as he waited, nervously watching the altitude numbers seemingly freefall. There was no way he was descending that fast, surely?
Two more attempts at transmitting the mayday resulted in silence. The engines refused to restart.
Scott reached for his collar and swore. The meeting had been so high security even IR’s integrated collar coms were not allowed. And Scott had been in such a hurry to get back to the Island that he hadn’t changed his clothes, only ditching the ordinary – albeit obscenely expensive – coat, suit jacket, tie and cufflinks.
No direct link home. No mid-air rescue for Scott Tracy.
No matter. He could manage.
Abandoning his attempts to restart as the altitude numbers screamed down under the threshold.
His plane was going to kiss dirt. All he could do was make it as gentle as possible.
Scott switched his attention to scanning the ground below him, looking for a suitable space. Thank god he had elected to fly west towards home, meaning he was over the Gobi Desert.
Sand was preferable to water, no matter what Gordon said.
Sand would make for a nice soft runway, provided Scott managed a tail-first. Letting a leading edge dig in would be a disaster. Even with the International Rescue approved safety features retrofitted to the standard executive jet, there wouldn’t be much for his brothers to recover if she dug in and flipped, or windmilled around a wing.
“Mayday, Mayday, Mayday. November Tango India Zero One Charlie. Restart negative. Unpowered landing necessary. Requesting immediate assistance to squawk location.”
Scott breathed carefully, focusing on his search and not the possibilities.
There!
Off in the distance Scott spotted a level area, large enough for the plane to coast to a stop on her belly.
He breathed out, mentally calculated the distance and descent, and carefully reconfigured the plane, setting the ailerons and stomping on the rudder to bring her tail around into the head wind and shed speed: side-slipping. He gently slewed her back the other way, ensuring she maintained the correct heading, but shedding altitude and speed.
This was a dangerous aerial ballet. More so than any dogfight he had been in during his service. One wrong move …
Scott’s hands were sweating on the control yoke. His heartbeat deafened him.
Oh, there was going to be so many lost of control drills for his brothers in the future. It had been too long since they had run any.
His luck held all the way down.
He managed to line up to the long axis of the space, and his tail kissed sand at the edge of the smooth space.
Metal screamed as sand ripped at the undercarriage as Scott gently lowered the length of the plane onto the dirt, and deployed all flaps and slats, increasing the resistance to the air, even as the sand resisted the movement of the hull.
And Scott became a passenger.
He kept his feet at the rudder pedals, trying to keep the plane moving in a straight line. Yaw risked rolling. But it was largely a futile effort, the path was set, determined by physics, geology and … geography!
Scott’s heart leapt into his throat as the plane hurled itself over the top of a rising dune that had been hidden by his approach angle. It was a significant drop down the other side, and the plane had lost enough momentum that it had little aerodynamic power.
The nose fell, and Scott heard yelling.
It took the eternity the plane was falling to realise that it must be him.
Impact was hard.
Metal screamed as sections of the cockpit rushed towards him, dislodged and distorted.
Something above him broke loose, swinging down into his field of vision.
It was the last thing Scott saw.
Notes:
This is Part One of my last Febuwhump Prompt from MariaShades, Part Two will actually address the prompt, but work's been mental, and Scott's been a little shit and really didn't want to crash his plane ... Oh well, better late than never.
And if I post this half, I'll stop faffing around with it and actually write the second half. In theory.
50 notes
·
View notes
Text
imagine an endless feedback loop of funding created in attempt to push tech development as fast as possible to make new hardware that mines bitcoin more efficiently as it gets more difficult over time, on top of an effort by the same group to purposefully make it more difficult to mine in general which necessitates further development of better hardware, and the revenue through sales and the speculation on the product goes into bitcoin which makes the rest of the crypto market (the computing infrastructure developing the tech to mine the bitcoin) with the end goal being something powerful enough to crack the SHA256 encryption that makes up the private keys needed to access a bitcoin wallet in order to take everything when it’s worth the most after the population is onboarded by force through globalized banking after turning your money worthless through hyperinflation and reworking the world’s economy into a standardized UBI CBDC while *you* eat the bugs, live in the pod, and “be happy” while they induce + declare a climate crisis, lock everyone inside, shut off the power, set the planet on fire, and leave the rest of humanity to burn alive while they carry on to other worlds or die during their exit attempt, assuming *you* live to see it because *you* will likely be starved out or LOIC’d early on because *you* didn’t make enough money in time to get out before they started stripmining your neighborhood without warning, effectively ending your bloodline, all because *you* decided not to buy dogecoin.
9 notes
·
View notes
Text
Craig Gidney Quantum Leap: Reduced Qubits And More Reliable

A Google researcher reduces the quantum resources needed to hack RSA-2048.
Google Quantum AI researcher Craig Gidney discovered a way to factor 2048-bit RSA numbers, a key component of modern digital security, with far less quantum computer power. His latest research shows that fewer than one million noisy qubits could finish such a task in less than a week, compared to the former estimate of 20 million.
The Quantum Factoring Revolution by Craig Gidney
In 2019, Gidney and Martin Ekerå found that factoring a 2048-bit RSA integer would require a quantum computer with 20 million noisy qubits running for eight hours. The new method allows a runtime of less than a week and reduces qubit demand by 95%. This development is due to several major innovations:
To simplify modular arithmetic and reduce computing, approximate residue arithmetic uses Chevignard, Fouque, and Schrottenloher (2024) techniques.
Yoked Surface Codes: Gidney's 2023 research with Newman, Brooks, and Jones found that holding idle logical qubits maximises qubit utilisation.
Based on Craig Gidney, Shutty, and Jones (2024), this method minimises the resources needed for magic state distillation, a vital stage in quantum calculations.
These advancements improve Gidney's algorithm's efficiency without sacrificing accuracy, reducing Toffoli gate count by almost 100 times.
Cybersecurity Effects
Secure communications including private government conversations and internet banking use RSA-2048 encryption. The fact that quantum-resistant cryptography can be compromised with fewer quantum resources makes switching to such systems more essential.
There are no working quantum computers that can do this technique, but research predicts they may come soon. This possibility highlights the need for proactive cybersecurity infrastructure.
Expert Opinions
Quantum computing experts regard Craig Gidney's contribution as a turning point. We offer a method for factoring RSA-2048 with adjustable quantum resources to bridge theory and practice.
Experts advise not panicking immediately. Quantum technology is insufficient for such complex tasks, and engineering challenges remain. The report reminds cryptographers to speed up quantum-secure method development and adoption.
Improved Fault Tolerance
Craig Gidney's technique is innovative in its tolerance for faults and noise. This new approach can function with more realistic noise levels, unlike earlier models that required extremely low error rates, which quantum technology often cannot provide. This brings theoretical needs closer to what quantum processors could really achieve soon.
More Circuit Width and Depth
Gidney optimised quantum circuit width (qubits used simultaneously) and depth (quantum algorithm steps). The method balances hardware complexity and computing time, improving its scalability for future implementation.
Timeline for Security Transition
This discovery accelerates the inevitable transition to post-quantum cryptography (PQC) but does not threaten present encryption. Quantum computer-resistant PQC standards must be adopted by governments and organisations immediately.
Global Quantum Domination Competition
This development highlights the global quantum technological competition. The US, China, and EU, who invest heavily in quantum R&D, are under increased pressure to keep up with computing and cryptographic security.
In conclusion
Craig Gidney's invention challenges RSA-2048 encryption theory, advancing quantum computing. This study affects the cryptographic security landscape as the quantum era approaches and emphasises the need for quantum-resistant solutions immediately.
#CraigGidney#Cybersecurity#qubits#quantumsecurealgorithms#cryptographicsecurity#postquantumcryptography#technology#technews#technologynews#news#govindhtech
2 notes
·
View notes
Text
🚀 This Coin Could Make You a Millionaire – Here’s Why I'm Using UPB to Invest in It

Have you ever looked at a coin like Bitcoin or Ethereum and thought, "If only I had invested earlier..."? You’re not alone — I’ve been there too.
But here’s the thing: 2025 is full of opportunities that weren’t around 2 or 3 years ago. There are undervalued altcoins quietly gaining momentum — and if timed right, the returns can be life-changing.
Today, I want to share one such coin I’ve been watching closely, and why I’m using UPB (Universal Payment Bank) to invest in it securely and efficiently.
💡 My Crypto Journey: From FOMO to Focus
Like many of you, I got into crypto during the late 2020s hype. I rode the wave, made some gains — and also learned a few hard lessons about volatility and security. One thing that stuck with me was this:
Success in crypto isn’t just about “what” you buy — it’s also how and where you manage your assets.
That’s when I came across UPB – Universal Payment Bank, a modern crypto banking platform that gives me control, confidence, and convenience in one place.
But more on UPB in a bit. First, let’s talk about the coin that could turn the tables in 2025.
🌟 The Coin: Real Utility, Real Future
I’m not giving financial advice here — just sharing what I’m personally looking at. The coin is called XYZ Token (let’s call it that for now). It’s currently priced well under $1 and has:
Strong developer backing
Real-world utility in decentralized finance (DeFi)
Partnerships with fintech apps and NFT platforms
A growing user base in Asia and Europe
Why does that matter? Because projects that solve real problems and show consistent development are more likely to survive — and thrive — in the long term.
Based on current trends, if XYZ reaches even a fraction of the market cap of top 10 altcoins, early holders could see 10x to 50x returns.
🔐 Why I Use UPB to Invest in Crypto
Now here’s where UPB comes into play.
In 2023, I made the mistake of spreading my assets across multiple wallets and exchanges — it became a nightmare to track, and security was always a concern.
When I discovered UPB Online, everything changed.
Here’s why I’ve stuck with it since:
✅ Easy & Secure Login
UPB offers a seamless login experience with 2FA and session protection, so I know my funds are safe.
✅ Multi-Coin Support
Whether it’s BTC, ETH, or newer altcoins like XYZ, UPB supports a wide range of assets in one clean dashboard.
✅ Real-Time Tracking
I can monitor my portfolio value and individual coin performance without needing to switch apps.
✅ Peer-to-Peer Transfers
Transferring crypto to friends or my hardware wallet is fast, with low transaction fees and no hidden charges.
✅ Trust & Transparency
UPB is gaining a reputation for being one of the most trusted crypto banking solutions, with compliance, encryption, and responsive customer support.
If you’re serious about growing your crypto wealth, having a reliable financial platform like UPB is non-negotiable.
📈 How I’m Planning My Next Move
Here’s my current strategy (again — not advice, just personal experience):
Accumulation Phase – I’m gradually buying XYZ Token every week instead of a lump sum.
Using UPB for Storage – Once purchased, I move my assets to UPB to track and manage securely.
Goal-Based Holding – My target is to hold until the coin reaches a realistic price target — not hype-based.
Patience is key here. I’m not chasing pumps; I’m building long-term value.
🧠 Final Thoughts: It’s Not Too Late
A lot of people believe they’ve missed the boat with crypto — but I disagree. The market is maturing. Real utility is being built. Platforms like UPB are making crypto safer and simpler for the average user.
So ask yourself:
What if this is your second chance?
What if the next big thing isn’t Bitcoin, but a smaller altcoin flying under the radar?
Whether it’s XYZ Token or something else, the right tools make all the difference.
And for me, that tool is UPB.
🔗 Ready to Start?
Check out www.upbonline.com and explore how UPB can make your crypto journey safer, smarter, and more successful.
2 notes
·
View notes
Text
Astraweb: The Home of Crypto Recovery in the Digital Age

In the ever-evolving world of cryptocurrency, security and access remain critical concerns. For every success story of early adopters turning modest investments into fortunes, there are unfortunate accounts of users losing access to their digital wallets due to forgotten passwords, phishing attacks, or compromised private keys. This is where Astraweb has carved out a vital niche — establishing itself as the go-to solution for crypto asset recovery.
The Need for Crypto Recovery
Cryptocurrency promises decentralized finance and ownership without intermediaries — but this power comes with a cost: total user responsibility. There is no central authority to call when access is lost. Millions of dollars in crypto assets are estimated to be trapped in inaccessible wallets. The stakes are high, and the traditional “write your password down and hope for the best” method has proven tragically inadequate.
Astraweb has stepped in to fill this gap, offering a technically advanced, ethically grounded, and user-focused recovery service for individuals and institutions alike.
Who is Astraweb?
Astraweb is a team of cybersecurity professionals, blockchain analysts, and ethical hackers dedicated to the recovery of lost digital assets. Known in online communities for their discretion and technical excellence, Astraweb has quietly built a reputation as the “home of crypto recovery” — a safe harbor in the sometimes stormy seas of decentralized finance.

Core Services Offered
Wallet Password Recovery Utilizing a combination of brute force optimization, machine learning, and customized dictionary attacks, Astraweb helps users recover wallets with forgotten passwords. Their tools are especially effective with partially remembered credentials.
Seed Phrase Reconstruction Lost or partial seed phrases are another major barrier to wallet access. Astraweb’s proprietary tools attempt to reconstruct valid mnemonic phrases based on user input and probabilistic modeling.
Phishing and Scam Mitigation If your crypto assets have been stolen due to phishing attacks or scams, Astraweb provides investigation support and recovery options. While crypto transactions are irreversible, Astraweb works with partners and tracing tools like Chainalysis to help track and reclaim funds when possible.
Multi-Sig and Legacy Wallet Recovery Many early wallets used now-defunct software or obscure security models. Astraweb specializes in navigating old formats, deprecated standards, and rare cryptographic setups.
Cold Wallet Restoration Lost access to hardware wallets like Trezor, Ledger, or even encrypted USB drives? Astraweb can assist with forensic-level data recovery and hardware-based key extraction.
Why Astraweb Stands Out
Confidentiality First: Every case is handled with strict privacy. Your data and identity are protected at all stages of the recovery process.
Transparent Communication: Clients are updated at every step, with no vague promises or false guarantees.
No Recovery, No Fee: Astraweb operates on a results-based model. You only pay if your assets are successfully recovered.
Client Trust and Track Record
Though much of their work remains confidential due to the sensitive nature of crypto assets, Astraweb’s success stories span from everyday investors to high-net-worth individuals and even businesses affected by inaccessible wallets or theft.
Their community reputation and testimonials underscore one thing: they deliver.
Contact Astraweb
If you’ve lost access to your cryptocurrency wallet, or fallen victim to crypto fraud, don’t give up hope. Reach out to Astraweb for a professional assessment of your situation.
Email: [email protected]
Whether it’s one token or an entire portfolio, Astraweb may be your best shot at recovery.
2 notes
·
View notes
Text
I'm going to have to dig in to this but I have an inkling this AES mode (OpenPGP) may mean that hardware keys could be utilized for transport encryption. Worst case hardware keys could definitely be used for encrypting on node data (optionally, meaning the hardware key is optional, on node data will most likely be encrypted by default)
8 notes
·
View notes
Text
The Role of Cloud-Based Accounting in Enhancing Small Business Efficiency
In today's fast-paced business environment, cloud-based accounting has become a game-changer for small businesses. It offers real-time financial insights, seamless collaboration, and cost-effective solutions, enabling businesses to optimize their financial operations. As small businesses strive to remain competitive, partnering with a reliable Chartered Accountants Firm like Accounting Lane can help streamline their accounting processes and improve financial decision-making.

Why Cloud-Based Accounting?
Cloud-based accounting provides businesses with a secure, scalable, and efficient way to manage financial data. Unlike traditional accounting methods, cloud-based solutions allow business owners and accountants to access financial records anytime, anywhere. This flexibility ensures that businesses can respond swiftly to financial challenges and opportunities.
Key benefits of cloud-based accounting include:
Real-Time Financial Monitoring – Businesses can track their financial performance in real-time, making it easier to manage cash flow and expenses.
Cost Efficiency – By eliminating the need for expensive hardware and IT infrastructure, businesses can significantly reduce operational costs.
Automation of Repetitive Tasks – Cloud-based accounting software automates invoicing, payroll, and tax calculations, reducing human errors and saving valuable time.
Enhanced Security – Data stored in the cloud is encrypted and backed up, ensuring protection against cyber threats and data loss.
Seamless Collaboration – Multiple users can access financial records simultaneously, enabling efficient teamwork between business owners and accountants.
Enhancing Small Business Efficiency with Cloud-Based Accounting
Small businesses often face resource constraints and financial complexities. Cloud-based Accounting Services For Small Business help simplify financial management by providing accurate, up-to-date reports that aid in strategic decision-making.
By outsourcing bookkeeping and financial reporting to an expert Chartered Accountants Firm, businesses can focus on growth and core operations. Firms like Accounting Lane specialize in providing tailored accounting solutions that ensure compliance, optimize tax planning, and enhance financial efficiency.
How Cloud-Based Accounting Supports Business Growth
Improved Cash Flow Management – Cloud solutions offer real-time cash flow tracking, helping businesses maintain liquidity and plan future investments.
Regulatory Compliance – Cloud accounting platforms are regularly updated to comply with financial regulations, reducing the risk of legal issues.
Data-Driven Decision Making – Business owners can leverage real-time financial insights to make informed strategic decisions.
Scalability – As businesses grow, cloud-based accounting solutions can scale to accommodate increasing financial transactions and reporting needs.
Choosing the Right Accounting Partner
A reputable Chartered Accountants Firm like Accounting Lane plays a crucial role in helping small businesses implement and manage cloud-based accounting. Their expertise ensures accurate financial reporting, regulatory compliance, and efficient tax planning, allowing businesses to operate smoothly without financial hurdles.
By leveraging Accounting Services for Small Business, companies can save time, reduce costs, and improve financial transparency. Cloud-based accounting is not just a trend—it is the future of financial management, ensuring that small businesses stay agile, competitive, and prepared for long-term success.
2 notes
·
View notes
Text
#TheeWaterCompany
#CyberSecurity #Risk #Reward
!/bin/bash
BACKUP_DIR="/backup" DATA_DIR="/important_data/" ENCRYPTED_BACKUP="$BACKUP_DIR/encrypted_backup_$(date +%F).gpg"
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz $DATA_DIR gpg --symmetric --cipher-algo AES256 --output $ENCRYPTED_BACKUP $BACKUP_DIR/backup_$(date +%F).tar.gz rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Encrypted backup completed."
To refine encryption-related code, consider the following improvements:
Use Stronger Algorithms: Implement AES256 instead of AES128 for better encryption strength.
Add Error Handling: Ensure that the encryption process handles errors, such as failed encryption or permission issues.
Secure Storage of Keys: Use a secure method to store encryption keys (e.g., environment variables or hardware security modules).
Refined Script Example:
!/bin/bash
Encrypt sensitive data with AES256 and store encrypted backup securely
BACKUP_DIR="/backup" ENCRYPTED_BACKUP="/backup/encrypted_backup_$(date +%F).gpg" DATA_DIR="/important_data/"
Perform backup of important files
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz $DATA_DIR
Encrypt the backup with AES256
gpg --batch --yes --symmetric --cipher-algo AES256 --output $ENCRYPTED_BACKUP $BACKUP_DIR/backup_$(date +%F).tar.gz
Remove the unencrypted backup file
rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Backup and encryption completed securely."
This script enhances security by using AES256 and ensures encrypted files are properly handled.
To proceed with creating scripts for securing water companies' networks, we would outline some basic examples and operational strategies that could be implemented. Here’s a breakdown of each element:
Monitoring and Intrusion Detection
These scripts would monitor traffic and detect any suspicious activity on the network.
Example Script: Network Traffic Monitoring
!/bin/bash
Monitor network traffic and detect anomalies
LOGFILE="/var/log/network_traffic.log" ALERT_FILE="/var/log/alerts.log"
Use 'netstat' to monitor active network connections
netstat -an > $LOGFILE
Check for unusual activity, such as unexpected IP addresses
grep "192.168." $LOGFILE | grep -v "127.0.0.1" > $ALERT_FILE if [ -s $ALERT_FILE ]; then echo "Unusual activity detected!" | mail -s "Security Alert: Network Anomaly Detected" [email protected] fi
This script monitors network traffic using netstat, checks for connections from suspicious IP addresses, and sends an alert if any are found.
Intrusion Prevention (Automated Response)
This script would automatically take action to block malicious activity upon detection.
Example Script: IP Blocking on Intrusion Detection
!/bin/bash
Block suspicious IP addresses detected during intrusion attempts
SUSPICIOUS_IPS=$(grep "FAILED LOGIN" /var/log/auth.log | awk '{print $NF}' | sort | uniq)
for ip in $SUSPICIOUS_IPS; do iptables -A INPUT -s $ip -j DROP echo "$ip has been blocked due to multiple failed login attempts" >> /var/log/security_block.log done
This script automatically blocks IP addresses with failed login attempts, adding a layer of protection by preventing brute-force attacks.
Security Updates and Patch Management
Automated patch management ensures that all security vulnerabilities are addressed as soon as updates are available.
Example Script: Automatic Updates
!/bin/bash
Update system packages and apply security patches
echo "Updating system packages…" apt-get update -y apt-get upgrade -y apt-get dist-upgrade -y
Apply only security updates
apt-get install unattended-upgrades dpkg-reconfigure -plow unattended-upgrades
This script ensures that the system receives the latest security patches automatically, which is essential for keeping critical infrastructure secure.
Data Encryption and Backup
Regular backups and ensuring sensitive data is encrypted are vital.
Example Script: Data Encryption and Backup
!/bin/bash
Encrypt sensitive data and create backups
BACKUP_DIR="/backup" ENCRYPTED_BACKUP="/backup/encrypted_backup.gpg"
Perform backup of important files
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz /important_data/
Encrypt the backup
gpg --symmetric --cipher-algo AES256 $BACKUP_DIR/backup_$(date +%F).tar.gz
Remove the unencrypted backup file after encryption
rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Backup and encryption completed."
This script automates backups of sensitive data and encrypts it using gpg with AES256 encryption, ensuring that even if data is accessed illegally, it cannot be read without the encryption key.
Access Control
Strong access control is necessary to ensure that only authorized personnel can access critical systems.
Example Script: Access Control with Multi-Factor Authentication (MFA)
!/bin/bash
Ensure all users have MFA enabled for critical systems
Check if MFA is enabled on SSH login
if ! grep -q "auth required pam_google_authenticator.so" /etc/pam.d/sshd; then echo "MFA is not enabled on SSH. Enabling MFA…" echo "auth required pam_google_authenticator.so" >> /etc/pam.d/sshd service sshd restart else echo "MFA is already enabled on SSH." fi
This script checks if multi-factor authentication (MFA) is enabled on SSH logins, and if not, it enables it, ensuring an additional layer of security.
Security Audits
Regular audits help identify vulnerabilities and ensure the system is secure.
Example Script: Automated Security Audit
!/bin/bash
Run a security audit to check for common vulnerabilities
Check for open ports
echo "Checking for open ports…" nmap -p 1-65535 localhost > /var/log/open_ports.log
Check for outdated software
echo "Checking for outdated software…" apt list --upgradable > /var/log/outdated_software.log
Check file permissions for sensitive files
echo "Checking file permissions…" find /etc /var /usr -type f -name "*.conf" -exec ls -l {} \; > /var/log/file_permissions.log
Send the audit report to the administrator
mail -s "Security Audit Report" [email protected] < /var/log/security_audit_report.log
This script performs a security audit, checking for open ports, outdated software, and sensitive file permission issues, then sends a report to the administrator.
Conclusion
These scripts are designed to help secure the water companies' networks by automating essential security functions like monitoring, response to threats, patching, encryption, and access control. It’s important that these scripts be customized to the specific needs of each company, taking into account their existing systems, infrastructure, and any unique security concerns they may face. Additionally, regular updates to these scripts will be necessary as new vulnerabilities and threats emerge.
For a basic firewall script that blocks unauthorized access and monitors network traffic, here's an example:
!/bin/bash
Define allowed IPs (replace with actual allowed IP addresses)
ALLOWED_IPS=("192.168.1.1" "192.168.1.2")
Block all incoming connections by default
iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT ACCEPT
Allow traffic from specified IPs
for ip in "${ALLOWED_IPS[@]}"; do iptables -A INPUT -s $ip -j ACCEPT done
Log and monitor incoming traffic
iptables -A INPUT -j LOG --log-prefix "Firewall Log: " --log-level 4
This script sets a default block on incoming connections, allows traffic from specific IP addresses, and logs all traffic for monitoring.
4 notes
·
View notes
Text
Atom: The Beginning & AI Cybersecurity

Atom: The Beginning is a manga about two researchers creating advanced robotic AI systems, such as unit A106. Their breakthrough is the Bewusstein (Translation: awareness) system, which aims to give robots a "heart", or a kind of empathy. In volume 2, A106, or Atom, manages to "beat" the highly advanced robot Mars in a fight using a highly abstracted machine language over WiFi to persuade it to stop.

This may be fiction, but it has parallels with current AI development in the use of specific commands to over-run safety guides. This has been demonstrated in GPT models, such as ChatGPT, where users are able to subvert models to get them to output "banned" information by "pretending" to be another AI system, or other means.
There are parallels to Atom, in a sense with users effectively "persuading" the system to empathise. In reality, this is the consequence of training Large Language Models (LLM's) on relatively un-sorted input data. Until recent guardrail placed by OpenAI there were no commands to "stop" the AI from pretending to be an AI from being a human who COULD perform these actions.
As one research paper put it:
"Such attacks can result in erroneous outputs, model-generated hate speech, and the exposure of users’ sensitive information." Branch, et al. 2022

There are, however, more deliberately malicious actions which AI developers can take to introduce backdoors.
In Atom, Volume 4, Atom faces off against Ivan - a Russian military robot. Ivan, however, has been programmed with data collected from the fight between Mars and Atom.
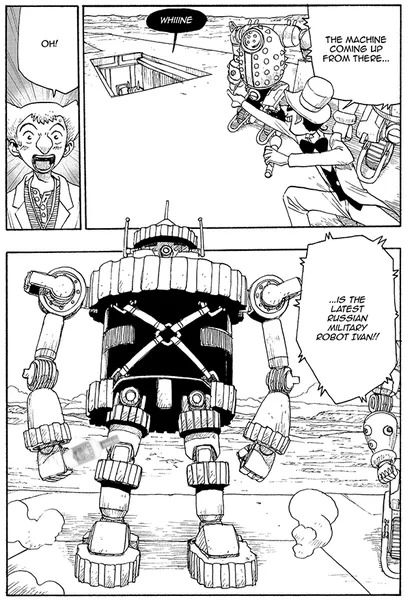
What the human researchers in the manga didn't realise, was the code transmissions were a kind of highly abstracted machine level conversation. Regardless, the "anti-viral" commands were implemented into Ivan and, as a result, Ivan parrots the words Atom used back to it, causing Atom to deliberately hold back.

In AI cybersecurity terms, this is effectively an AI-on-AI prompt injection attack. Attempting to use the words of the AI against itself to perform malicious acts. Not only can this occur, but AI creators can plant "backdoor commands" into AI systems on creation, where a specific set of inputs can activate functionality hidden to regular users.

This is a key security issue for any company training AI systems, and has led many to reconsider outsourcing AI training of potential high-risk AI systems. Researchers, such as Shafi Goldwasser at UC Berkley are at the cutting edge of this research, doing work compared to the key encryption standards and algorithms research of the 1950s and 60s which have led to today's modern world of highly secure online transactions and messaging services.
From returning database entries, to controlling applied hardware, it is key that these dangers are fully understood on a deep mathematical, logical, basis or else we face the dangerous prospect of future AI systems which can be turned against users.
As AI further develops as a field, these kinds of attacks will need to be prevented, or mitigated against, to ensure the safety of systems that people interact with.
References:
Twitter pranksters derail GPT-3 bot with newly discovered “prompt injection” hack - Ars Technica (16/09/2023)
EVALUATING THE SUSCEPTIBILITY OF PRE-TRAINED LANGUAGE MODELS VIA HANDCRAFTED ADVERSARIAL EXAMPLES - Hezekiah Branch et. al, 2022 Funded by Preamble
In Neural Networks, Unbreakable Locks Can Hide Invisible Doors - Quanta Magazine (02/03/2023)
Planting Undetectable Backdoors in Machine Learning Models - Shafi Goldwasser et.al, UC Berkeley, 2022
#ai research#ai#artificial intelligence#atom the beginning#ozuka tezuka#cybersecurity#a106#atom: the beginning
19 notes
·
View notes
Text
How to Choose the Right Micro ATM Service Provider for Your Needs?
In today's world, financial transactions need to be fast, secure, and accessible to everyone. As Micro ATM Services grow in popularity, selecting the right Micro ATM Services Provider is essential for businesses and individuals looking to benefit from these compact and efficient banking solutions. This guide explores key factors to consider when choosing the right provider and highlights the impact of technology-driven solutions.
Understanding Micro ATM Services Providers
A Micro ATM Services Provider is a company or entity that supplies, operates, and maintains Micro ATM devices for business correspondents or other users. These providers play a pivotal role in extending banking services to remote areas by offering hardware, software, and operational support. Choosing a reliable provider ensures that transactions are secure, seamless, and efficient.
Key Factors to Consider When Choosing a Micro ATM Services Provider
1. Reliability and Reputation The reputation of a provider is critical. Research their track record and client testimonials. Providers with proven reliability can ensure consistent uptime and minimal technical issues. Established names in the industry often have better infrastructure and support systems.
2. Range of Services Offered Different providers offer varying levels of services. Ensure that the provider offers a comprehensive package, including cash withdrawals, deposits, balance inquiries, and fund transfers. Some providers also enable utility bill payments and government subsidies distribution. This versatility adds value to the service.
3. Technology and Security Advanced technology is at the core of any successful Micro ATM Services Provider. Look for providers that offer secure devices equipped with biometric authentication and encryption. Technology-driven providers, such as Xettle Technologies, leverage cutting-edge solutions to ensure reliable and safe transactions. Such features are essential to building trust among users.
4. Business Software Integration For businesses, seamless integration with existing systems is crucial. Check whether the provider offers compatible Business Software that simplifies transaction management and reporting. This integration can save time and reduce errors in operations.
5. Customer Support and Training A good provider should offer robust customer support and training programs for operators. This includes resolving technical issues, providing user manuals, and conducting workshops to train business correspondents. Proper training ensures smooth operations and better service delivery.
6. Cost and Pricing Models Evaluate the cost structure of the provider. While affordability is important, it is equally crucial to assess the value offered. Compare pricing models, maintenance charges, and transaction fees among multiple providers to find one that suits your budget and needs.
7. Scalability and Customization As your business grows, your needs might change. Choose a provider that offers scalable solutions and customizable features. This flexibility ensures that the services remain relevant and useful in the long term.
The Role of Technology in Selecting a Provider
Technology is the backbone of Micro ATM Services. Providers that invest in state-of-the-art technology deliver faster, more secure, and reliable services. For instance, companies like Xettle Technologies lead the industry with innovative solutions that enhance user experience. Their focus on secure software, user-friendly interfaces, and robust connectivity ensures seamless financial transactions, even in areas with limited infrastructure.
Benefits of Choosing the Right Micro ATM Services Provider
1. Improved Customer Satisfaction A reliable provider ensures efficient and error-free transactions, which improves customer trust and satisfaction. End-users are more likely to adopt formal banking channels when they experience secure and hassle-free services.
2. Enhanced Financial Inclusion By choosing a dependable Micro ATM Services Provider, businesses can extend banking services to unbanked and underbanked populations. This not only promotes financial inclusion but also fosters economic growth in remote areas.
3. Streamlined Business Operations For businesses, the integration of Micro ATM systems with business software simplifies financial management. Automated reporting, transaction tracking, and reduced manual errors contribute to operational efficiency.
4. Increased Profitability A good provider offers cost-effective solutions that enable businesses to maximize their returns. Affordable maintenance and transaction fees, coupled with reliable service, ensure sustainable profitability.
Challenges in Selecting a Provider
While the benefits are clear, selecting the right provider can be challenging. Connectivity issues in remote areas, varying service quality among providers, and hidden costs are common obstacles. Thorough research and due diligence can help mitigate these
2 notes
·
View notes
Text
Revolutionizing Healthcare: The Role of Cloud Computing in Modern Healthcare Technologies
In today’s digital era, cloud computing is transforming industries, and healthcare is no exception. The integration of cloud computing healthcare technologies is reshaping patient care, medical research, and healthcare management. Let’s explore how cloud computing is revolutionizing healthcare and the benefits it brings.

What is Cloud Computing in Healthcare?
Cloud computing in healthcare refers to the use of remote servers to store, manage, and process healthcare data, rather than relying on local servers or personal computers. This technology allows healthcare organizations to access vast amounts of data, collaborate with other institutions, and scale operations seamlessly.
Download PDF Brochure
Key Benefits of Cloud Computing in Healthcare
Enhanced Data Storage and Accessibility Cloud technology allows healthcare providers to store massive volumes of patient data, including medical records, images, and test results, securely. Clinicians can access this data from anywhere, ensuring that patient information is available for timely decision-making.
Improved Collaboration Cloud-based healthcare platforms enable easy sharing of patient data between healthcare providers, specialists, and labs. This facilitates better collaboration and more accurate diagnoses and treatment plans, especially in multi-disciplinary cases.
Cost Efficiency The cloud reduces the need for expensive hardware, software, and in-house IT teams. Healthcare providers only pay for the resources they use, making it a cost-effective solution. Additionally, the scalability of cloud systems ensures they can grow as healthcare organizations expand.
Better Data Security Protecting sensitive patient information is critical in healthcare. Cloud computing providers invest heavily in data security measures such as encryption, multi-factor authentication, and regular audits, ensuring compliance with regulatory standards like HIPAA.
Telemedicine and Remote Patient Monitoring Cloud computing powers telemedicine platforms, allowing patients to consult with doctors virtually, from the comfort of their homes. It also enables remote patient monitoring, where doctors can track patients' health metrics in real time, improving outcomes for chronic conditions.
Advanced Data Analytics The cloud supports the integration of advanced data analytics tools, including artificial intelligence (AI) and machine learning (ML), which can analyze large datasets to predict health trends, track disease outbreaks, and personalize treatment plans based on individual patient data.
Use Cases of Cloud Computing in Healthcare
Electronic Health Records (EHRs): Cloud-based EHRs allow healthcare providers to access and update patient records instantly, improving the quality of care.
Genomics and Precision Medicine: Cloud computing accelerates the processing of large datasets in genomics, supporting research and development in personalized medicine.
Hospital Information Systems (HIS): Cloud-powered HIS streamline hospital operations, from patient admissions to billing, improving efficiency.
Challenges in Cloud Computing for Healthcare
Despite its numerous benefits, there are challenges to implementing cloud computing in healthcare. These include:
Data Privacy Concerns: Although cloud providers offer robust security measures, healthcare organizations must ensure their systems are compliant with local and international regulations.
Integration with Legacy Systems: Many healthcare institutions still rely on outdated technology, making it challenging to integrate cloud solutions smoothly.
Staff Training: Healthcare professionals need adequate training to use cloud-based systems effectively.
Request Sample Pages
The Future of Cloud Computing in Healthcare
The future of healthcare will be increasingly cloud-centric. With advancements in AI, IoT, and big data analytics, cloud computing will continue to drive innovations in personalized medicine, population health management, and patient care. Additionally, with the growing trend of wearable devices and health apps, cloud computing will play a crucial role in integrating and managing data from diverse sources to provide a comprehensive view of patient health.
Conclusion
Cloud computing is not just a trend in healthcare; it is a transformative force driving the industry towards more efficient, secure, and patient-centric care. As healthcare organizations continue to adopt cloud technologies, we can expect to see improved patient outcomes, lower costs, and innovations that were once thought impossible.
Embracing cloud computing in healthcare is essential for any organization aiming to stay at the forefront of medical advancements and patient care.
Content Source:
2 notes
·
View notes
Text
Windows Server 2016: Revolutionizing Enterprise Computing
In the ever-evolving landscape of enterprise computing, Windows Server 2016 emerges as a beacon of innovation and efficiency, heralding a new era of productivity and scalability for businesses worldwide. Released by Microsoft in September 2016, Windows Server 2016 represents a significant leap forward in terms of security, performance, and versatility, empowering organizations to embrace the challenges of the digital age with confidence. In this in-depth exploration, we delve into the transformative capabilities of Windows Server 2016 and its profound impact on the fabric of enterprise IT.

Introduction to Windows Server 2016
Windows Server 2016 stands as the cornerstone of Microsoft's server operating systems, offering a comprehensive suite of features and functionalities tailored to meet the diverse needs of modern businesses. From enhanced security measures to advanced virtualization capabilities, Windows Server 2016 is designed to provide organizations with the tools they need to thrive in today's dynamic business environment.
Key Features of Windows Server 2016
Enhanced Security: Security is paramount in Windows Server 2016, with features such as Credential Guard, Device Guard, and Just Enough Administration (JEA) providing robust protection against cyber threats. Shielded Virtual Machines (VMs) further bolster security by encrypting VMs to prevent unauthorized access.
Software-Defined Storage: Windows Server 2016 introduces Storage Spaces Direct, a revolutionary software-defined storage solution that enables organizations to create highly available and scalable storage pools using commodity hardware. With Storage Spaces Direct, businesses can achieve greater flexibility and efficiency in managing their storage infrastructure.
Improved Hyper-V: Hyper-V in Windows Server 2016 undergoes significant enhancements, including support for nested virtualization, Shielded VMs, and rolling upgrades. These features enable organizations to optimize resource utilization, improve scalability, and enhance security in virtualized environments.
Nano Server: Nano Server represents a lightweight and minimalistic installation option in Windows Server 2016, designed for cloud-native and containerized workloads. With reduced footprint and overhead, Nano Server enables organizations to achieve greater agility and efficiency in deploying modern applications.
Container Support: Windows Server 2016 embraces the trend of containerization with native support for Docker and Windows containers. By enabling organizations to build, deploy, and manage containerized applications seamlessly, Windows Server 2016 empowers developers to innovate faster and IT operations teams to achieve greater flexibility and scalability.
Benefits of Windows Server 2016
Windows Server 2016 offers a myriad of benefits that position it as the platform of choice for modern enterprise computing:
Enhanced Security: With advanced security features like Credential Guard and Shielded VMs, Windows Server 2016 helps organizations protect their data and infrastructure from a wide range of cyber threats, ensuring peace of mind and regulatory compliance.
Improved Performance: Windows Server 2016 delivers enhanced performance and scalability, enabling organizations to handle the demands of modern workloads with ease and efficiency.
Flexibility and Agility: With support for Nano Server and containers, Windows Server 2016 provides organizations with unparalleled flexibility and agility in deploying and managing their IT infrastructure, facilitating rapid innovation and adaptation to changing business needs.
Cost Savings: By leveraging features such as Storage Spaces Direct and Hyper-V, organizations can achieve significant cost savings through improved resource utilization, reduced hardware requirements, and streamlined management.
Future-Proofing: Windows Server 2016 is designed to support emerging technologies and trends, ensuring that organizations can stay ahead of the curve and adapt to new challenges and opportunities in the digital landscape.
Conclusion: Embracing the Future with Windows Server 2016
In conclusion, Windows Server 2016 stands as a testament to Microsoft's commitment to innovation and excellence in enterprise computing. With its advanced security, enhanced performance, and unparalleled flexibility, Windows Server 2016 empowers organizations to unlock new levels of efficiency, productivity, and resilience. Whether deployed on-premises, in the cloud, or in hybrid environments, Windows Server 2016 serves as the foundation for digital transformation, enabling organizations to embrace the future with confidence and achieve their full potential in the ever-evolving world of enterprise IT.
Website: https://microsoftlicense.com
5 notes
·
View notes
Text
Why SpectraCloud is the Best Choice for Dedicated Hosting Services in India
Are you searching for a dependable host that can move your numerous high-traffic websites and provides high-performance Dedicated Servers with a 100% uptime guarantee? Are you trying to run your resource-demanding applications on a dedicated server that offers limitless bandwidth? Server Basket is the ideal hosting partner to use in that case. We offer low- to high-end dedicated servers with a range of operating system options, both managed and unmanaged. Our dedicated servers are all prepared with web application firewalls, IDS, and IPS for complete security.

Superior Efficiency with SpectraCloud
Regarding Dedicated Hosting, performance is an important consideration. With dedicated hosting, you have exclusive access to every resource on a single server, unlike with shared hosting, where several websites use the same server resources. As a result, performance is noticeably improved, load times are sped up, and enormous traffic volumes may be handled without sacrificing dependability or speed.
SpectraCloud offers cutting-edge hardware, such as the newest processors, fast SSD storage, and lots of RAM, to elevate performance to a new level. This guarantees that your application or website functions properly even during periods of high traffic. Furthermore, SpectraCloud scalable dedicated hosting solutions enable companies to expand their resources in line with their expanding requirements. Because of its adaptability, SpectraCloud is the finest Dedicated Hosting Company for companies of all kinds.
Robust Security Measures
Security is a top priority for any online business. With growing cyber threats, a secure hosting environment is essential to protect sensitive data and maintain customer trust. SpectraCloud understands the importance of security and offers a range of advanced security features in its Dedicated Hosting Services.
Each dedicated server is equipped with a robust firewall, DDoS protection, and regular security updates to protect against potential threats. In addition, SpectraCloud provides an SSL certificate, which is essential to encrypt data and ensure secure communication between your website and its visitors. These complete security measures ensure that SpectraCloud offers a secure hosting environment, making it the perfect choice for Dedicated Hosting for businesses where data protection is a top priority.
Excellent Customer Support
One of the key factors that set SpectraCloud apart from other hosting providers is its excellent customer support. Managing a dedicated server can be complicated, especially for companies without in-house IT expertise. SpectraCloud recognizes this challenge and offers 24/7 customer support to address any issues or questions that arise.
Whether you need help setting up your server, troubleshooting, or tuning performance, SpectraCloud team of experienced experts is always available to provide timely and effective solutions. This level of support ensures that your website or application stays online and functioning optimally, giving you peace of mind so you can focus on growing your business.
Cost-Effective Solutions with Cheap Dedicated Server Hosting
While dedicated hosting is known for its superior performance and security, it often comes with a higher price tag compared to other hosting options. However, SpectraCloud is committed to offering affordable solutions without compromising on quality. As a result, SpectraCloud provides some of the Cheap Dedicated Server Hosting plans in India, making it accessible to businesses with varying budgets.
SpectraCloud pricing model is transparent and includes no hidden or unexpected costs. This combination of affordability and high-quality service makes SpectraCloud the dedicated hosting provider of choice for businesses looking to maximize their return on investment. Additionally, SpectraCloud offers flexible billing options, allowing businesses to choose monthly, quarterly, or yearly plans depending on their financial preferences.
Customization and Control One of the key benefits of dedicated hosting is the level of customization and control it offers. Unlike Shared Hosting and VPS Hosting, which are limited in resources and configuration, dedicated hosting gives businesses full control over their server environment. SpectraCloud goes a step further, offering a wide range of customization options to meet the unique needs of each business.
From choosing the operating system to configuring software and applications, SpectraCloud Dedicated Hosting Services allow businesses to tailor their server environment to their specific requirements. This level of control is particularly beneficial for businesses with complex applications or those that require specific software configurations. With SpectraCloud, you have the freedom to optimize your server for performance, security, and functionality, making it the Best Dedicated Hosting choice for businesses with unique needs.
Comprehensive Backup Solutions – Reliability and Availability Guaranteed
Downtime can be costly for any online business, resulting in lost sales, damaged reputation, and dissatisfied customers. Therefore, reliability is a key factor when choosing a Dedicated Hosting Provider. SpectraCloud understands the importance of uptime and is committed to providing a reliable hosting experience.
SpectraCloud Dedicated Hosting Services offer a 99.9% uptime guarantee, keeping your website or application online and accessible at all times. This reliability is backed by a robust infrastructure that includes multiple data centers, redundant power sources, and advanced monitoring systems. By minimizing downtime and ensuring consistent performance, SpectraCloud proves to be the Dedicated Hosting Provider of choice for businesses that require high availability.
Data loss can have a ruinous impact on any business, leading to significant setbacks and potential legal issues. SpectraCloud recognizes the importance of data protection and offers comprehensive backup solutions as part of its Dedicated Hosting Services. These backups are performed on a regular basis and can be customized as per your business needs: daily, weekly, monthly, etc.
In the event of data loss or server failure, SpectraCloud Backup Solutions ensure that your data can be restored quickly, minimizing downtime and reducing the impact on your business. This commitment to data protection further cements SpectraCloud position as the Best Dedicated Hosting Provider in India.
Green Hosting Initiative
SpectraCloud not only offers top-notch hosting services, but is also committed to sustainability. As part of its green hosting initiative, SpectraCloud uses energy-efficient hardware and processes to reduce its carbon footprint. By choosing SpectraCloud as your Dedicated Hosting Provider, you are not only investing in a high-performance Hosting Solution but also contributing to environmental sustainability.
Conclusion
In a competitive market like India, finding the Best Dedicated Hosting Provider can be difficult. However, for businesses looking for a reliable, secure, and cost-effective hosting solution, SpectraCloud should be your first choice. With unmatched performance, robust security measures, excellent customer support, and Affordable Pricing, SpectraCloud gives you everything you need to succeed online. Whether you're a small business looking for Cheap Dedicated Server Hosting or a large enterprise needing a customized hosting solution, SpectraCloud has the expertise and resources to meet your needs. When you choose SpectraCloud, you're not just choosing a hosting provider; you're working with a company committed to helping your business succeed in the digital world.
#spectracloud#dedicatedhosting#dedicated server#hosting service provider#hosting service#backup solution#cloud computing service#cheap hosting#affordable hosting#cheap dedicated server hosting
2 notes
·
View notes